Creating and Editing a Linux Patch Scan Configuration (content-based only)
A Linux patch scan configuration defines how a patch scan will be performed for the content-based method. Security Controls provides two predefined configurations for content-based patch scanning.
- All Patches: Specifies that the agent will scan for all patch types. A patch group will not be used.
- Security Patches: Specifies that the agent will scan for only security patches. The agent will not scan for bug fixes or enhancements, and a patch group will not be used.
For contentless patching Linux machines, a scan for all missing patches is included in all Linux Patch Tasks, so there is no separate patch scan.
You cannot edit the predefined configurations. If the predefined configurations are not adequate for your needs, you can create a custom configuration.
To work with a custom Linux patch scan configuration, do one of the following:
- To create a new patch scan configuration, click New > Linux Patch (Content-Based) > Patch Scan Configuration.
- To edit an existing patch scan configuration, in the Linux Patch Configurations (Content-Based) list, double-click the configuration name.
| Field | Descriptions |
|---|---|
|
Name |
The name that you wish to assign to this configuration. |
|
Path |
This box is used to specify the folder path that this configuration will reside in within the Linux Patch Scan Configurations list in navigation pane. If you do not specify a path, the configuration will reside at the root level of the My Linux Patch Scan Configurations list. For more details, see Organizing Linux Patch Groups and Configurations. |
|
Description |
A description of the configuration. |
|
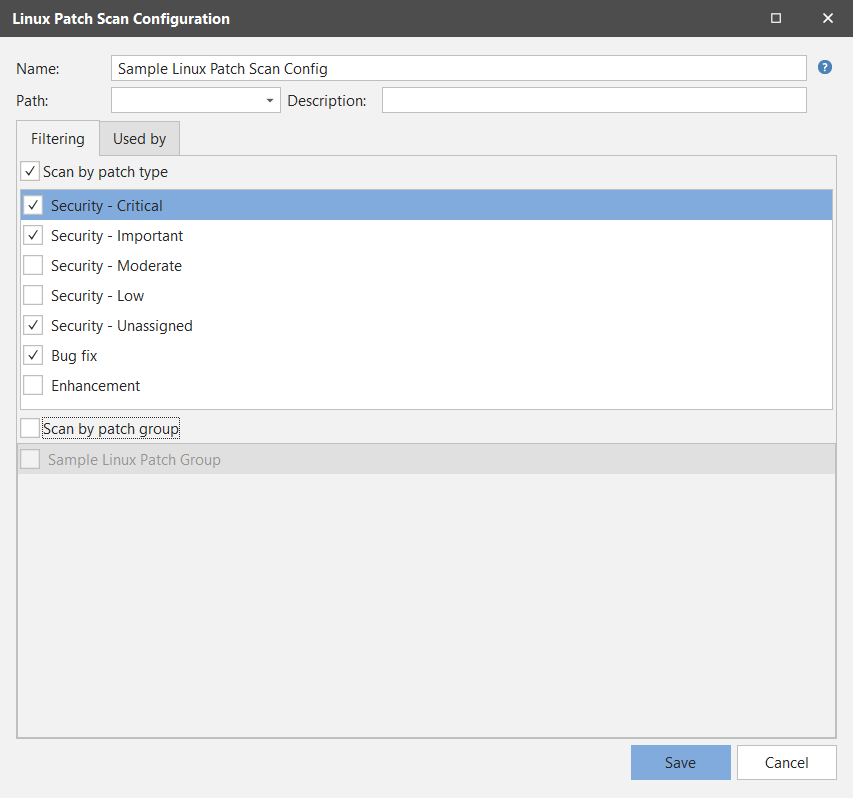
Filtering tab |
There are two different options available on this tab: Scan by patch type and Scan by patch group. You can select one or both options.
|
|
Used By tab |
This tab shows you the agent policies that are currently using this configuration. This is important to know if you are considering modifying the configuration, as it tells you which agents are affected. |